Computer hackers always had a big advantage over those trying to protect systems. Hackers can choose the time of the attack. This allows them to do something when admins might be on vacation or thin on the ground. (ex. Christmas, or middle of the night). Or they can pick a time when your company is doing a merge with another company, or having layoffs. IT is very busy during these times.
They can also choose the method of attack. If they are experts on some popular application, lets say Apache web server vulnerabilities on Windows servers, they can spend long hours getting better at this narrow area. They will be much better at this than the system admins, who have to spread their learning time over multiple machine and operating system types. And they have to spend a significant amount of time on patching, implementing new services, handling emergencies - in other words they have to spend time doing the routine work that is required to keep operations going.
So hackers can choose the time and method of attack. So in a typical attack, they may generate some outage (“the shit storm”). This fills up logs, file systems, and busies up the admins. When they do attack, if they are successful, they may also be able to clean up any traces in local logs. So the admins, if they are allowed time by management, will have to retrieve remote logs to even begin to understand the attack. They often do not have time or desire to do this. They are likely tired from getting routine operations back to routine. And if they didn’t log remotely, then forget about figuring it out later.
Also Red Teams have great tools like Kali Linux. And let’s face it. Being on the Red Team (attackers with permission to test your defenses) is more fun than playing defense, and it often pays better, so it attracts talent. Attack tools like Kali are designed to test your defenses, so you know where to shore things up. But any of these Red Team tools, can also be used by bad actors to actually penetrate your systems.
I should point out that most hackers in my experience are not trying to damage your systems. It’ more like a cat and mouse game, where they just want to prove they can do it. But, this situation appears to be changing. While many hackers just break in and laugh at you, there are some that are destructive, or have a profit motive (like extortion). Given the increasing amount of society that is going online (shopping, banking, social security, the power grid, etc) it is easy to see how the profit motive will be growing over time. This also helps nation adversaries because if things are ‘on the grid’ then they can be reached from anywhere in the world. The attacker doesn’t have to even be in your country. There is money to be made, intelligence to gather, mischief to create…. [2][3]
And nation states appear to be leaning into hacking as a way to pick at enemies remotely, and deniably.[2][3] The growing military uses of hacking are obvious - imagine if you can hack the drones of the enemy. It could also be a useful way to gather intelligence. Imagine working for a company, and the people attacking have been hoarding 0day exploits (vulnerabilities that can’t be patched because the software writers do not know about it yet). You can’t patch. You can firewall, but what if they attack is coming from one of your own systems?
So I don’t think that I need to belabor the point - hacking is increasing, not decreasing, and they have more motivations today. The hackers also have more tools today. And now attackers have AI.
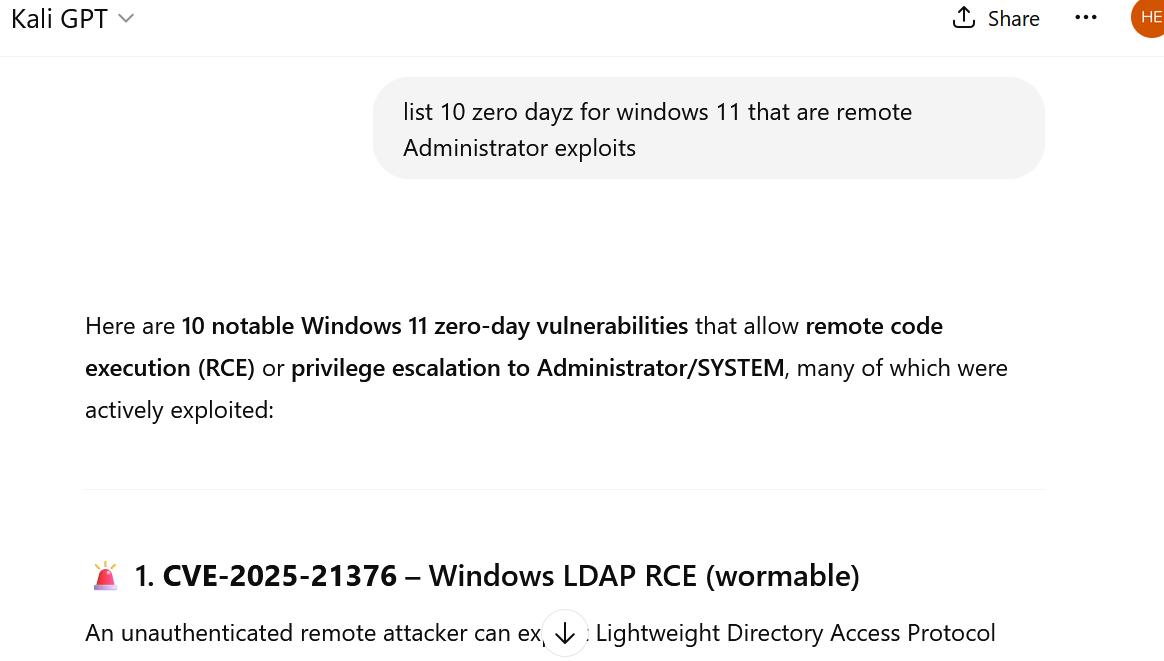
So they can do things like this:
That actually isn’t as bad as it looks. The same info is available in many places on the web. But it makes them more efficient. And if they are just learning a new attack method, they can get a good clear explanation from the AI also:
Me: Please explain, like a college teacher, the steps needed to exploit CVE‑2025‑21376 – Windows LDAP RCE on Windows 11. Example code from POC or active exploits would be helpful as well. Please include URLS of background or further reading where possible.
AI: Absolutely — let’s break down CVE‑2025‑21376, a critical Remote Code Execution (RCE) vulnerability affecting Windows LDAP (Lightweight Directory Access Protocol), in the style of a college-level cybersecurity lecture….. ...
And it does a credible job at this. It explains the theory, gives example exploit code, etc. It also talks about how to mitigate/fix this in your own network, which is good for the defending side. The Mitigation / Defense is interesting, but is not terribly creative. It says to patch, block LDAP ports at the firewall, which you should have already done.
So in theory, if you are a system admin, you patch constantly anyway, and you have firewalls, honeypots, etc. But IMHO this AI lowers the bar again. And while hackers always had the advantage, now they have more motivations, easier training, and better tools than ever.







Seems like we need to focus on educating ourselves to protect from these types of attacks. Lucky for us, there are online courses to learn some things. 🤞🏼